
15 Apr (E)SAE DEEP DIVE SERIES PART 9 – Privilege Admin Workstation (PAW)
This month our blog is about Privilege Admin Workstations (PAW). PAWs are used to separate the work environment for sensitive activities such as server or Active Directory administration from the “office” work environment for surfing, editing e-mail and other non-administrative activities.
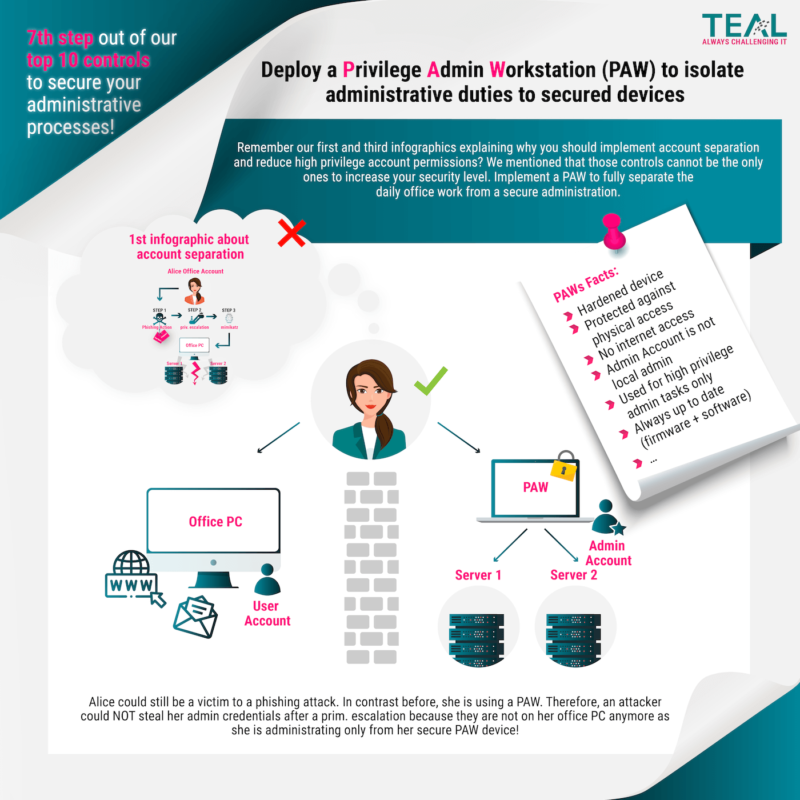
The overall goal of this separation is to protect against Internet-based attacks and other attack vectors. The logic is simple, if I do not surf the Internet with my work device, I cannot catch a virus on the Internet.
Microsoft described before the restructuring of the Privilege Access documentation in detail what PAWs are, why you should use them and which variants of them exist, as well as their advantages and disadvantages. Fortunately, you can still read the article in the Internet Archive. In the current documentation, unfortunately, the topic comes a bit short. In our article, we limit ourselves to a very summary of the issues and go into more detail about implementation problems and possible real-life solutions.
Privileged work environments must be protected against…
… attacks from the Internet:
Most attacks originate directly or indirectly from the Internet and use the Internet as a medium to exfiltrate data from the corporate network or to control “agents” via a command and control infrastructure. Isolating the PAW from the Internet is an essential element in ensuring that the PAW is not compromised.
…attacks from the corporate network:
Since most employees today need the Internet to perform their jobs, complete isolation is utopian. Thus, most devices and accounts are exposed to threats from the Internet. As a consequence, a PAW must be protected against attacks from compromised assets in the production environment. Therefore, the use of management tools and accounts that can access PAWs to protect and monitor these specific workstations must be minimized.
… a manipulation of the supply chain
Even if it is impossible to eliminate all risks of manipulation for hardware and software, critical attack vectors can be minimized considerably. As an example, check all installation media (trusted source principle) and work with a trustworthy and reputable supplier for hardware and software.
… physical attacks
Because PAWs can be mobile and used outside the physically secured environment, they must be protected from physical attacks.
… too high complexity
The fact that security and usability are often at odds is unfortunately nothing new. In the context of PAWs, this carries the risk that administrators will look for “shortcuts” and workarounds when working with PAWs is too complicated to better manage the undoubtedly high workload. A compromise must therefore be reached between security and usability.
What are the PAW variants
Dedicated hardware
The classic variant of the PAW is a separate device. This is separate from the administrator’s office PC. This is the most secure variant since the environments are physically separated and thus there is no attack path via software vulnerabilities. The probability that the administrator mixes up the devices and enters his admin credentials on a possibly compromised device is also low. However, it also means that the administrator must place two devices on the desk or take them home if the employee wants to work in the home office.
VM
To reduce this double burden on administrators and to reduce costs, it is quite possible to use virtualization technology to save one device. However, the PAW must run directly on the hardware and the office environment in a VM:

A comparable scenario is the office environment on a terminal server:
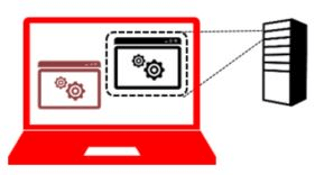
Jump Server
Jump servers for administrative activities are widely used and therefore the thought is obvious to declare this jump server as PAW. However, this is a fallacy. If the jump server is accessed from the office environment, the credentials are just as compromised as if you were administering directly from the office PC:

If you do not want to install all the necessary tools on the PAW, the jump server is still a valid variant if it is accessed from a PAW. This variant also simplifies the auditing of administrative activities:

Privilege Access Solution
Many customers introduce privilege access solutions and think they are safe. However, the same principle applies here as with Jump Servers. As long as the solution is accessed with normal office devices, there is a risk:

# Only if accessed by means of PAW, the risk does not exist:

Please don’t get us wrong, privilege access solutions have their justification and should be used. This is only about access to the solution.
Hurdles to real-life implementation
The description in the first part of the blog sounds plausible at first and also quite easy to implement. However, when you get down to the details, you will encounter some problems that need to be solved somehow. In the following, we describe some challenges and possible solutions that we have already encountered in customer scenarios. The categories chosen by Microsoft fit very well here.
Challenges in protecting against attacks from the Internet:
(File) Exchange
One of the most important measures to protect the PAW is not to surf the Internet with it. In real admin life, however, we look up most error messages on the Internet first, download a script for analysis or solution from somewhere, and execute it. Of course, all this will not work if neither the server nor the PAW have access to the Internet.
A solution to the problem can be to allow a controlled exchange between the office working environment and the PAW / the systems to be administered. The simplest variant here is a file server in the same tier (Tiering Blog-Post) as the systems to be administered, to which only the appropriate admins have access. A virus scanner should automatically scan the files as they are written.
Of course, this has an impact on usability, more on that below.
Remote Access
In times of Corona, home office work is more relevant than ever, but even before that, many admins worked from outside the company premises, especially when on-call duty was necessary. Thus, the possibility of remote dial-in is required, and the device also needs Internet access for this purpose. How can this be reconciled with the principle that PAWs do not have Internet access?
One possibility is to enter a proxy locally (which does not exist) and define a proxy exception only for the endpoint of the remote dial-in platform. Often the administrators are also local admin of the PAW (more on this under supply chain), so such a configuration can of course be bypassed. Usability issue here as well.
Remote Support
What to do if you get stuck? Most larger companies have support contracts with the manufacturers of their software. When working with the support companies, you often reach the point where you would like to look at the system together with the expert.
Here again, you have to weigh usability and security in relation to local conditions. One option is to install a meeting software on the PAW and release the corresponding ports. If the meeting servers are located in your own network and the number of ports is manageable, the risk may be acceptable. However, if you use a meeting service from the cloud, the situation may be different.
If you don’t want to use the meeting client, you can still hold the conference on your office device and record the PAW’s screen content using a webcam.
If someone knows a better variant, he can write it in the comments. 😊
Challenges in protecting against attacks from the corporate network
This point actually includes almost all protective measures that go beyond the lack of an Internet connection. In order not to go beyond the scope of this blog, we would only like to address one question at this point: What hardening settings should I implement on the PAW and how do I ensure that they are actually implemented?
We completely rely on the #nocodehardening initiative which we also support since its foundation. We combine hardening recommendations from common baselines such as BSI, CIS, DISA and the Microsoft Security Baseline. We roll out the settings to the PAWs using PowerShell DSC. The rollout and management is supported with the Enforce Suite. What exactly the Enforce Suite is and how it can be used in detail, you will learn in a separate blog post. Just so much in advance – we are big fans and absolutely convinced of our Enforce Suite! 😊
Challenges in protecting against supply chain tampering
This aspect is more extensive than it seems at first glance. On the one hand, one must technically ensure that the hardware and software are free of malware, which in itself is not easy. The other part of the discussion, however, is who is “one”?
Responsibility
Who is organizationally responsible for providing the PAWs for the different tier levels? The more critical the tier, the fewer admins there should be. Especially for Tier 0, there should only be a handful of selected specialists. Since they have to make sure that your workstation is free of malware, this inevitably leads to the fact that they also have to install it themselves and if an image is used for this purpose, they have to create and maintain this image themselves (or at least be present to check it). This issue needs to be addressed organizationally. Again, we will go into this further in the Usability chapter.
Hardware
Making sure that the hardware is free of malware is usually very difficult. Usually, the admins in the company do not have the knowledge and tools to detect whether a rootkit or similar is installed on the hardware.
One way to achieve a certain level of protection here is not to procure the devices from the dealer around the corner or from the cheapest supplier from abroad, but to include the aspect of security and control at the dealer as a selection criterion in the purchase.
Software
Things are no less difficult when it comes to software. Some manufacturers publish hashes together with the files. This way, you can at least check whether the files have been manipulated during transport. If a manufacturer does not publish hashes, you can help yourself by downloading the software twice on different devices with different internet connections and creating the hashes yourself. But if a backdoor (hello Solarwinds *wink smiley*) has been installed by the manufacturer can’t be checked that way.
If someone here knows a better and viable alternative we are all ears 😊
Challenges in protecting against physical attacks
The most important thing here is that the administrator handles the work device responsibly. As a general rule, the PAW should not be left unattended anywhere; it is best to lock it up when leaving the workplace and certainly not to leave it at Starbucks.
But you can also increase security through technical measures. Encrypting the hard drive with Bitlocker, for example, is an absolute “must”.
Furthermore, you should consider making the USB ports unusable. This can be done by software, but there are also special locks for the ports. However, you have to consider that the admin is not restricted too much.
Challenges in protecting against excessive complexity
The measures described in the last section all sound right and sensible in themselves. However, the human factor should not be lost sight of during planning and implementation.
If it takes 15 minutes to log into the environment when you are on standby and then you have to copy the error message to a device in 10 steps and then search for it on the Internet, your motivation will be very limited.
Even with less pronounced restrictions, the duration for individual activities will increase. Management must take this into account when planning personnel.
Conclusion
In our view, PAWs are one of the essential building blocks for protecting the credentials of administrators and should be used by every company. However, we have also shown in the article that a perfect (or almost perfect) protection is unfortunately not realistically achievable in practice and one must proceed with moderation and purpose so that the employees work with it and do not look for easier (=our) ways to do their job. For those who find this too complicated on their own, we can help 😊.
Sieh dir diesen Beitrag auf Instagram an
Sieh dir diesen Beitrag auf Instagram an
LATEST POSTS
-
(E) SAE DEEP DIVE SERIE Part 2 – Secured VMs in an ESAE environment with VMWare
In our January blog, we started an SAE deep dive series and explained how to use Hyper-V as a secure hypervisor in an (E)SAE scenario. Since by far not all our customers use Hyper-V, but many also use VMWare...
15 June, 2020 -
(E) SAE Deep Dive Series Part 1: Hyper-V Host Guardian Service (HGS) and Shielded VMs in an EASE Environment
After the success of the first ESAE series, we decided to launch a deep dive series in which we go into a little more detail on various measures....
16 January, 2020 -
(E) SAE DEEP DIVE SERIES Part 3 – Separate admin accounts
After Hyper-V HGS and VM protection with VMWare, now the third part of our (E) SAE Deep Dive Series follows. Maybe you follow us on LinkedIn, Xing, Facebook, Instagram or Twitter and ...
15 July, 2020




























