
13 Jun ESAE series part 6 – New Microsoft ESAE architecture – TEAL analyzes the changes…
TEAL has been intensively involved with Microsoft Active Directory Security projects since its foundation. We were able to work with several customers and did presentations on how business processes and the architecture of a Microsoft infrastructure can be changed to mitigate Pass the Ticket / Pass the Hash attacks. Our recommendations are based on the publicly available information on Microsoft’s own offering “ESAE – Enhanced Secure Administration Environment”, aboutwe have been blogging regularly since the beginning of 2018:
Part 1 – https://www.teal-consulting.de/en/2018/05/02/esae-series-part-1-introduction/
Part 2 – https://www.teal-consulting.de/en/2018/05/03/esae-series-part-2-customer-situation-and-architecture/
Part 5 – https://www.teal-consulting.de/en/2019/03/15/esae-series-part-5-windows-ipsec/
The publicly available information can be found under the keyword “Securing privileged access” – LINK (https://docs.microsoft.com/en-us/windows-server/identity/securing-privileged-access/securing-privileged-access). In February 2019, Microsoft updated the content and adapted it to current circumstances. We take this as an opportunity to evaluate the new measures and make our evaluation.
At first glance, it is noticeable that Microsoft is placing more emphasis on the implementation path than on the description of the target state. It becomes clear that Quick Wins should be implemented fast, which is reflected in the following three phases:
- Phase 1: First 30 days quick wins with meaningful positive impact.
- Phase 2: 90 days significant incremental improvements.
- Phase 3: Ongoing security improvement and sustainment.”
Phase 1:
In the first phase, quick wins such as LAPS for local password management, dedicated admin devices (PAWs) for administration and account separation will be implemented. What is noticeable, however, is that a cloud service (Azure ATP – Advanced Thread Protection – https://azure.microsoft.com/de-de/features/azure-advanced-threat-protection/) is to be introduced in the first 30 days.
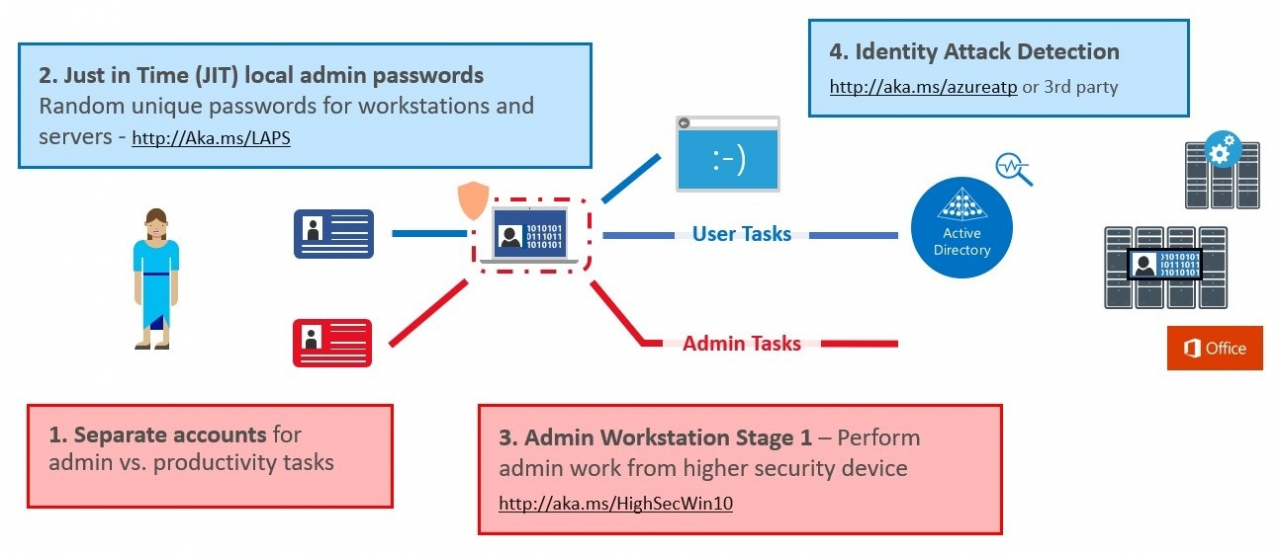
With Azure ATP, information from the local infrastructure is sent to the service and analyzed for anomalies. For example, user, device and resource behavior are monitored and anomalies are immediately reported via a feed or resolved independently (if desired). The big advantage here is, of course, that you have a powerful tool from the start to recognize whether you are being attacked or not. ATP can be licensed individually or as part of the Enterprise Mobility + Security E5 Suite (https://www.microsoft.com/de-de/enterprise-mobility-security/compare-plans-and-pricing).
To use Azure ATP, the company needs a working Azure Tenant and must constantly send data to the cloud. From our point of view, this can be problematic for companies that either do not yet use cloud services at all or may first have to agree with data protection officers and works councils what may be synchronized. Especially in large companies, it is rarely possible to introduce new services within 30 days. Furthermore, such a cloud service must also fit into budget planning. Budget planning is usually completed by the end of the year and the use of Enterprise Mobility and Security E5 Suite may not even be planned yet. These additional costs also have to be approved before they can be implemented. However, services like Azure ATP offer a great added value and should definitely be included in the long-term planning!
Phase 2:
Further hedging measures are to be introduced over the next 90 days. Again, further cloud services are included in the scope.
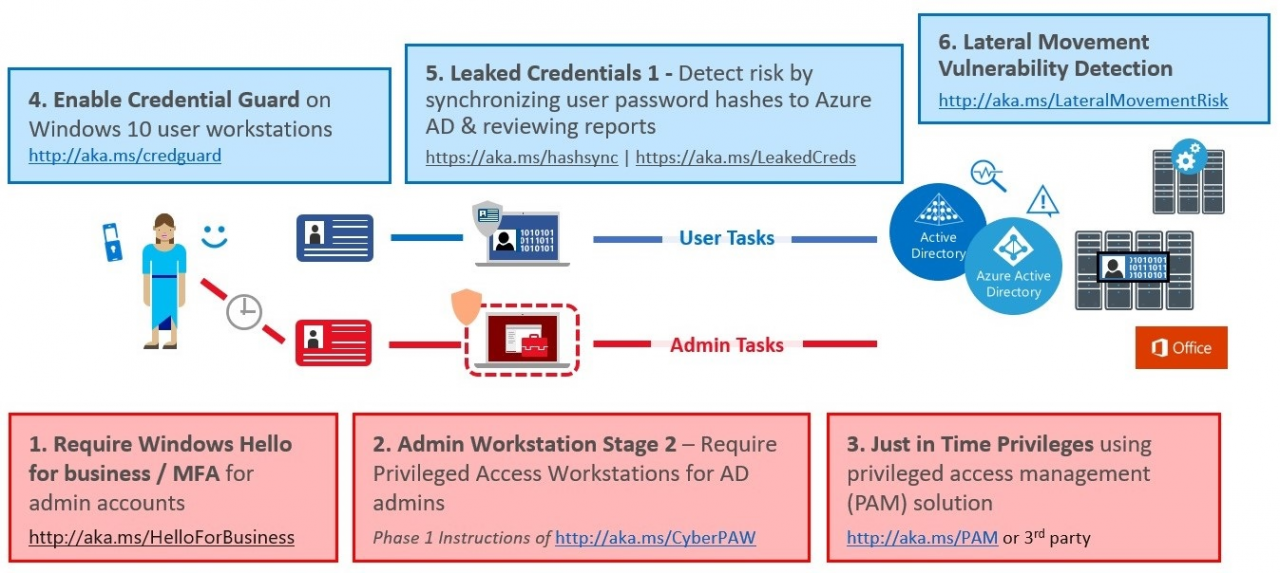
With Azure AD Identity Protection and Azure ATP Lateral Movement Vulnerability Detection, two services are introduced that also focus on anomaly detection. This makes sense. On one of my past projects, I asked a Microsoft Security PFE what he considered to be the three most important measures in an ESAE project. His answer – Detection, Detection and Detection. Only if you can even recognize that you are being attacked you can react to it. The statement is correct, however, in our customer assessments we have learned again and again that in most environments there is no security baseline or an outdated one. Beginning with outdated and partly unpatched systems, over unimplemented hardening baselines up to missing account separation.
For such environments, we believe it would be more effective to eliminate these rudimentary shortcomings before introducing new services.
Furthermore, Just in Time Privileges will be introduced. Here Microsoft refers to the MIM/PAM for ADDS and Azure PIM for Azure AD. Also here the use of Azure services is clearly in the focus. Before the update a dedicated Admin Forest and the use of Shadow Principal Objects was recommended (which we also described in our part 3 of the ESAE blog – https://www.teal-consulting.de/index.php/blog/easa-serie-teil-3-privileged-access-management-und-shadow-principals-feature).
The question arises again, what does a customer do who does not use Azure and does not want to use it? If you take a closer look at the new documentation, you will still find the Admin Forest Model (https://docs.microsoft.com/en-us/windows-server/identity/securing-privileged-access/securing-privileged-access-reference-material).
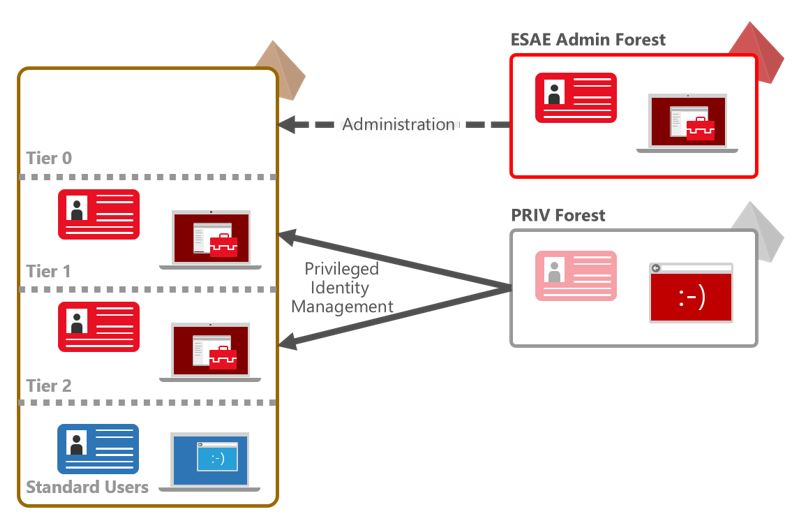
From our point of view it still makes sense in certain scenarios to set up a dedicated admin forest and not to use cloud services exclusively.
Phase 3
In the last phase, a continuous security process is to be introduced which evaluates the controls introduced and adjusts them if necessary.
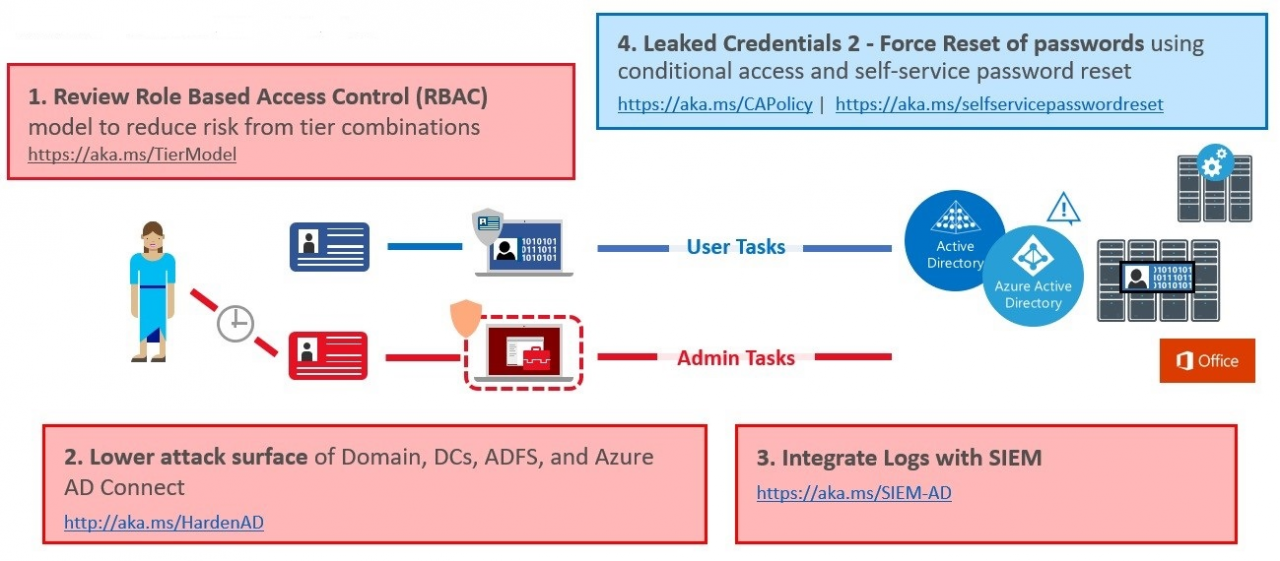
Especially topics like SIEM usecases are very important and can also help to detect attacks. In addition, the protection of the services used by GPOs and other configurations is in the foreground. As already mentioned above, from our point of view it is necessary to implement a good security baseline as early as possible and reasonably planned GPOs are part of it. The basis for this can be the Security Baseline templates from Microsoft (https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-security-baselines), or various Best Practice recommendations from security authorities or experts.
Conclusion
The new documentation gives the impression that significant results can already be achieved after the first 120 days. This is certainly true, but especially in enterprise environments it requires the use of considerable financial and human resources. Furthermore, cloud services are increasingly used to detect attacks, which is not desired in all organizations.
Most of the customers we have seen so far do not have a comprehensive security baseline rolled out, patch management is sometimes a bit patchy and things like regular password changes, account segregation etc. are usually not available in their entirety. In addition, there is usually a need to raise awareness as to why all these measures need to be introduced. In our opinion, an AD Security project depends on whether the operating team and the management can be convinced to introduce and use new working methods.
In order to tailor the procedure and the measures individually to the customer, we usually start an engagement with a three-day workshop in which we explain the threat scenarios in detail on the first day, analyse the current environment on the second day and develop a target architecture, and create a roadmap with quick wins and long-term measures on the third day and coordinate them with the customer. If we have woken up your interest and you would like more information about our Active Directory Assessment, please feel free to contact us at info@teal-consulting.de!
Source: freepik.com
LATEST POSTS
-
(E) SAE DEEP DIVE SERIE Part 2 – Secured VMs in an ESAE environment with VMWare
In our January blog, we started an SAE deep dive series and explained how to use Hyper-V as a secure hypervisor in an (E)SAE scenario. Since by far not all our customers use Hyper-V, but many also use VMWare...
15 June, 2020 -
(E) SAE Deep Dive Series Part 1: Hyper-V Host Guardian Service (HGS) and Shielded VMs in an EASE Environment
After the success of the first ESAE series, we decided to launch a deep dive series in which we go into a little more detail on various measures....
16 January, 2020 -
(E) SAE DEEP DIVE SERIES Part 3 – Separate admin accounts
After Hyper-V HGS and VM protection with VMWare, now the third part of our (E) SAE Deep Dive Series follows. Maybe you follow us on LinkedIn, Xing, Facebook, Instagram or Twitter and ...
15 July, 2020




























