13 Nov Assume Breach – Secure IT Infrastructure using the TEAL Security Assessment

13 Nov Assume Breach – Secure IT Infrastructure using the TEAL Security Assessment
The damage caused by cyber attacks is increasing every year and it is only a matter of time before a company is successfully attacked. Not only Microsoft says again and again that a paradigm shift is necessary in dealing with IT security. “Assume Breach” is more present than ever. Our world is becoming more and more complex, cloud services have become an integral part of most IT landscapes and security boundaries are regularly shifting as a result of merger or acquisition projects. One could say that data theft is more likely than getting the flu and in any case more expensive.
(Source)
That’s why we have been blogging since May 2018 about secure IT infrastructure based on the Microsoft ESAE model. We call our form of the Microsoft ESAE model, Secure Administration Environment (SAE), because most enterprise environments are heterogeneously equipped with Windows, Linux and MacOS and therefore have to be considered holistically. In the SAE blog series, we explain the basics of secure IT operations and discuss the individual technical and organizational security measures. The blog series was very well received by our customers and we were often asked if we could explain the SAE principles in more detail and help plan a project to improve security levels.
We took this as an opportunity to create a standardized workshop, our SAE Security Assessment.
The aim of the workshop is:
- to explain the techniques and methods of modern attackers to the participants.
- to communicate possible security controls.
- to analyze the customer’s live environment.
- to create a prioritized action plan to improve the security level.
So the goals are defined, but what are we going to do concretely in the workshops?
Typically, we plan three days for the workshop, but we can also individualize the content as needed.
Day 1
The first priority is to build up knowledge. From our point of view, it is essential that administrators understand exactly what attack scenarios and methods they are dealing with. Secure administration requires both technical and organizational measures. We explain these and very quickly come to the conclusion that administration is becoming more complex. It is therefore even more important that the people who are affected by the effects really understand why they are necessary. Only then, they adhere to the new working principles and not look for “shortcuts”.Furthermore, securing an IT infrastructure is a continuous process. Measures must always be questioned and adapted to current needs. Also the administrators must be trained regularly and the know-how must be kept up to date.
Specifically, we explain the Cyber Kill Chain and give an overview of tools and attacks from each phase. Since most customers have a heterogeneous environment of Linux and Windows servers, but the most important identity and authorization management for most of our customers is Microsoft Active Directory, we go into more detail on Mimikatz and Bloodhound.
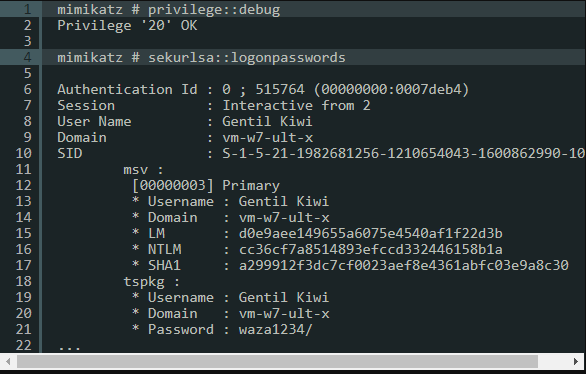
It’s always nice to see the astonished faces of the participants in the live demo when they see their plaintext passwords in Mimikatz’s own log file, or how easy it is to perform a pass-the-hash or pass-the-ticket attack with Mimikatz.
Plain text password with mimikatz (http://blog.gentilkiwi.com/mimikatz)
After the threat situation has been explained, the rest of the day is about how to protect yourself effectively. A central component is the Tiering-Model, in which all systems are categorized into different Tiers. Each tier has assigned certain security controls and organizational processes. The following applies: The lower the tiering level, the worth protecting are the assets (Tier 0 = crown jewels).
The most important measures are discussed and explained in detail. Experience has shown that this part is quite individual for each customer, as we also focus on the needs of the workshop participants here. Once all measures have been understood, we conclude the day and make final preparations for the live assessment of the customer environment the next day.
Day 2
After the first day focused on theory, the second day focuses exclusively on the customer’s productive environment. We first get to know the environment by working through a specific questionnaire with the customer. Here we not only get to know the environment, but can also present some recommendations and best practices.
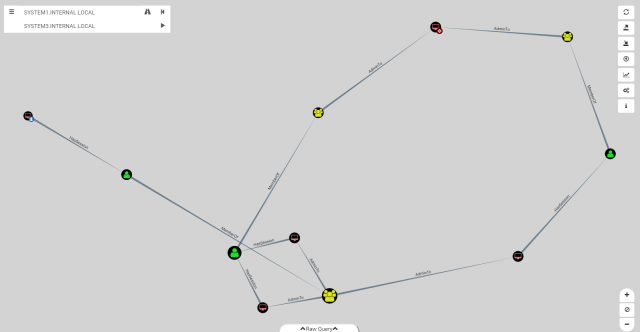
We then go into the production environment together and run Bloodhound. Bloodhound gives a graphical overview of the attack paths to privileged accounts.
https://posts.specterops.io/introducing-the-adversary-resilience-methodology-part-two-279a1ed7863d
It is one thing to test Bloodhound in a demo environment, another thing to run the tool in your “own” production environment and to have a complex authorization structure graphically displayed that has grown over the years. By now at the latest, a common understanding is usually achieved as to why, for example, a tiering of the administration is meaningful and important.
However, Bloodhound is not the only tool we use. Another great tool is Pingcastle, which creates a detailed report about the Active Directory. Here, too, there are numerous suggestions for improvement.
https://www.pingcastle.com/documentation/healthcheck/
But we don’t just rely on tools that examine the Active Directory. We have collected numerous Open Source scripts and execute them automatically by our wrapper and thus collect data about service accounts, file servers, operating system configuration and much more…
For us it means to evaluate log files and prepare the last day of the assessment.
Day 3
Two days of intensive work and learning are over, but what kind of insights have we gained now and what will we do next? Day 3 gives the answer. We go through the results of the assessment in detail, explain what we found and discuss it together. In addition, now is the time to take a closer look at the list of the numerous measures from day 1. We assign the possible measures to the results of the assessment and determine…
- …whether a special measure makes the customer environment more secure
- …how much effort the implementation would cause
- …which priority the measure gets
Once all the results have been worked through, we prepare a results document that contains all the data collected and describes a roadmap for implementation. This is now the basis for a continuous increase in IT security in the company. The customer decides what can be implemented independently and which topics require external support.
Conclusion
We have been working with the SAE model for several years now and have gained a lot of experience with our customers. The Security Assessment is a very good starting point to initiate a sustainable change.
If you are also interested in a Security Assessment, please contact us! We are happy to help you.
Further information can also be found in our short overview of the Security Assessment.
In our experience, the successful implementation of a SAE project stands or falls with the employees. So that administrators get to know the processes and tools better and gain practical experience, we will also be offering a SAE training next year. More about this in the near future… 😊
LATEST POSTS
-
(E) SAE DEEP DIVE SERIE Part 2 – Secured VMs in an ESAE environment with VMWare
In our January blog, we started an SAE deep dive series and explained how to use Hyper-V as a secure hypervisor in an (E)SAE scenario. Since by far not all our customers use Hyper-V, but many also use VMWare...
15 June, 2020 -
(E) SAE Deep Dive Series Part 1: Hyper-V Host Guardian Service (HGS) and Shielded VMs in an EASE Environment
After the success of the first ESAE series, we decided to launch a deep dive series in which we go into a little more detail on various measures....
16 January, 2020 -
(E) SAE DEEP DIVE SERIES Part 3 – Separate admin accounts
After Hyper-V HGS and VM protection with VMWare, now the third part of our (E) SAE Deep Dive Series follows. Maybe you follow us on LinkedIn, Xing, Facebook, Instagram or Twitter and ...
15 July, 2020