15 Sep (E)SAE DEEP DIVE SERIES PART 12 – System hardening
In our last article of the “(E)SAE Deep Dive” series, we would like to look at the topic of system hardening today. Operators of critical infrastructures (CRITIS), for example, must ensure that “the state of the art” is implemented. This of course encompasses much more than system hardening, although this is a very important but often neglected discipline. But it is not only CRITIS operators that need to protect their infrastructure; other companies should also take the issue of system hardening seriously. For example, many cyber insurance companies will only reimburse the full amount after an incident if a customer was not negligent. Now, of course, we at TEAL are not lawyers, but we do think that system hardening needs to be a central part of any cybersecurity strategy. But what is system hardening?
Attentive readers of our blog may remember the article about the #NoCodeHardening initiative. The goal of the initiative is to raise awareness for the topic of system hardening and to provide support for its implementation.
There, system hardening is explained as follows:
In summary, system hardening is intended to configure and monitor necessary security settings on IT systems.
Why to harden systems?
In addition to legal requirements or minimizing the risk of insurance failure, there are other good reasons for operating IT systems securely. As an example, we would like to take a look at the Server Message Block (SMB) protocol. SMB is used for file and print services and typically runs over port 445 and 139, respectively. Over the years, there have been several versions of SMB. Back in the mid-90s, SMB V1 was released, followed by SMB V2. The current version is SMB V 3.1.1.
Microsoft itself, explains SMB like this:
SMB V1 was already attacked by hackers 20 years ago, but also newer known ransomware variants like WannCry or EternalBlue used SMB V1 vulnerabilities to compromise systems. Even the SolarWinds hack, so well known, had exploited SMB as a source of origin. Common hardening standards have long recommended disabling SMB V1. In the best case, only V3 or higher is used, although V2 is not yet to be explicitly disabled in the current hardening recommendations. Furthermore, however, SMB must also be configured sensibly and securely, as recommended by the Center for Internet Security (CIS), for example:
- Update and Patch Against SMB Vulnerabilities
- Block SMB at the Network Level
- Restrict and Protect SMB at the Host Level
- Use Secure Authentication Methods for SMB
- Enable Encryption for SMB
In total, more than 20 security settings are recommended to secure SMB. These include settings that at first glance have nothing to do with SMB, but are nevertheless necessary for full protection. So, across multiple topics, several hundred settings quickly add up to ensure that an IT system is configured securely.
But where is an administrator supposed to get all these settings?
Sources for system hardening settings
So that administrators do not have to repeatedly research and analyze down to the last detail how services and systems are configured securely, there are various industry standards. These are regularly updated for the common operating systems and services and specify security settings.
We would like to briefly introduce the most common ones from our point of view.
Best Practice Baseline industry standards
CIS
The Center for Internet Security (CIS)
… is one of the best sources for hardening settings. CIS Benchmarks document best practices for the particular safe configuration of a target system. There are more than 100 CIS Benchmarks available from over 25 product families, developed through a consensus-based process. Cybersecurity experts and professionals from around the world come together for development.
The settings are available in two levels:
- Level 1 helps an organization quickly minimize its attack surface while prioritizing business functionality. Level 1 compliance for all assets is the minimum level of security an organization should strive for.
- Level 2 is a more robust set of requirements that prioritizes the enterprise’s security posture by promoting “defense in depth.” Level 2 compliance is essential for organizations with high security and compliance requirements, such as those in highly regulated industries. Of course, Level 2 compliance is more complex and resource intensive.
MICROSOFT
Microsoft also regularly publishes
… new security baselines for all current operating systems and server services. Users can obtain, view and also adapt the baselines via the Security Compliance Tool Kit.
The current security baseline update for Windows 10, for example, came out in May 2021 along with Windows 10 version 21H1. For servers, the current hardening can be found in server version 20H2.
A baseline always contains different settings for the following topics:
| Internet Explorer | User settings | Credential Guard |
| Bitlocker | Defender | Member Server |
| Computer settings | Domain Security | Domain Controller |
Microsoft usually specifies settings that do not cause any major problems and is therefore also smaller than the CIS rule set, for example. Nevertheless, even with a Microsoft baseline, careful analysis is required before settings are applied in productive environments.
BSI
The Center for Internet Security (CIS)
… is also a good source for obtaining security settings. However, unlike CIS or Microsoft, it is not the case that you can download ready-made sets of rules for the most common products. The BSI works with the basic protection catalogs, which describe a target image of a secure system. This is very good, but also a lot to read.
The SiSyPHus project, which describes how to secure a Windows 10 system, deserves special mention. In addition to excellent documentation, there are also ready-made Windows 10 security settings as GPOs:
BSI – SiSyPHuS Win10: Windows 10 Group Policy Objects for Guidelines on Hardening and Logging (bund.de)
However, settings for domain controllers or other server systems are unfortunately still missing at this point.
CIS
The Center for Internet Security (CIS) is one of the best sources for hardening settings. CIS benchmarks document best practices for the particular secure configuration of a target system. There are more than 100 CIS benchmarks available from over 25 product families, developed through a consensus-based process. Cybersecurity experts and professionals from around the world come together for development.
There are two levels of settings:
- Level 1 helps an organization quickly minimize its attack surface while prioritizing business functionality. Level 1 compliance for all assets is the minimum level of security an organization should strive for.
- Level 2 is a more robust set of requirements that prioritizes the enterprise’s security posture by promoting “defense in depth.” Level 2 compliance is essential for organizations with high security and compliance requirements, such as those in highly regulated industries. Of course, Level 2 compliance is more complex and resource intensive.
Microsoft
Microsoft also regularly publishes new security baselines for all current operating systems and server services. Users can obtain, view and also adapt the baselines via the Security Compliance Tool Kit.
The current security baseline update for Windows 10, for example, came out in May 2021 along with Windows 10 version 21H1. For servers, the current hardening can be found in server version 20H2.
A baseline always contains various settings for the following topics:
- Internet Explorer
- Bitlocker
- Computer settings
- User settings
- Defender
- Domain Security
- Credential Guard
- Member Server
- Domain Controller
Microsoft usually specifies settings that do not cause any major problems and is therefore also smaller than the CIS rule set, for example. Nevertheless, even with a Microsoft baseline, careful analysis is required before settings are applied in productive environments.
BSI
The German Federal Office for Information Security (BSI) is also a good source for obtaining security settings. However, unlike CIS or Microsoft, it is not the case that you can download ready-made sets of rules for the most common products. The BSI works with the basic protection catalogs, which describe a target image of a secure system. This is very good, but also a lot to read.
The SiSyPHus project, which describes how to secure a Windows 10 system, deserves special mention. In addition to excellent documentation, there are also ready-made Windows 10 security settings as GPOs:
BSI – SiSyPHuS Win10: Windows 10 Group Policy Objects for Guidelines on Hardening and Logging (bund.de)
However, settings for domain controllers or other server systems are unfortunately still missing at this point.
Select and roll out curing settings
After looking at the different vendors for security settings, the question remains how do I choose the right settings for me, how do I combine standards if necessary, and most importantly, how do I roll them out securely and check that the settings are adhered to.
Classically, many would probably use Group Policy (GPO) for this, but in our view this is an outdated technology. Instead, we recommend using PowerShell Desired State Configuration Management (DSC) for this – by the way, Microsoft has also been moving in the direction of DSC instead of GPO for years.
To make system hardening as easy as possible, we at TEAL use the Enforce Suite product to harden and monitor systems.
We would like to explain how this works and will of course be happy to help with any questions 😊.
First, we divide the project into three rough parts that can always be repeated system group by system group. This is mainly because different systems need different hardening settings… On an IIS-based WebServer, I may need to make different security settings than on a database system.
- Check requirements
- Are there specific requirements that need to be taken into account during hardening? For example, is it a KRITIS company or a company that is monitored by BaFin?
- In addition, are there internal guidelines that are specified by Compliance, IT Security or other departments?
- Define individual baseline based on common industry standards
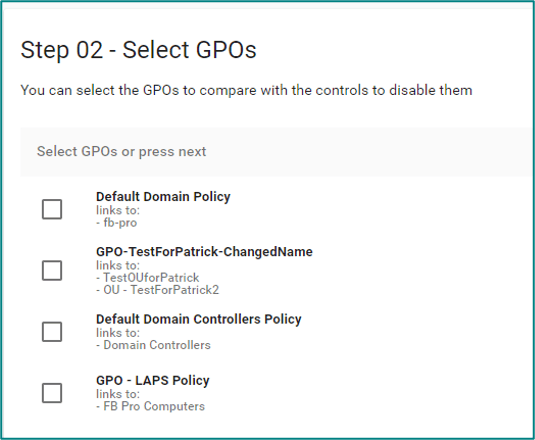
- The aim is to generate a suitable hardening set based on the requirements, which is then applied to a specific system group (e.g. role-oriented). For this purpose, various ready-made standards can be used in the Enforce Suite:

-
- Once the standards are selected, a specific standard can be prioritized. For example, if three standards are selected and all three configure a certain value, the setting of the prioritized standard is automatically used.
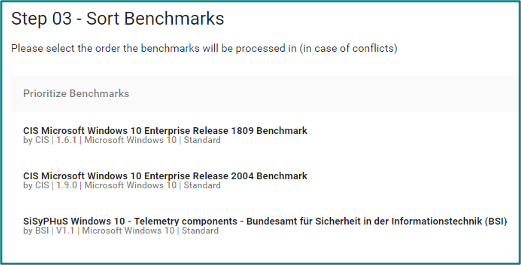
-
- If conflicts between standards occur, they can be resolved manually. E.g. CIS switches a certain setting on, but Microsoft switches it off.

- If conflicts between standards occur, they can be resolved manually. E.g. CIS switches a certain setting on, but Microsoft switches it off.
-
- However, it can also happen that settings are already configured via group policies. This is also detected by Enforce.

- However, it can also happen that settings are already configured via group policies. This is also detected by Enforce.
-
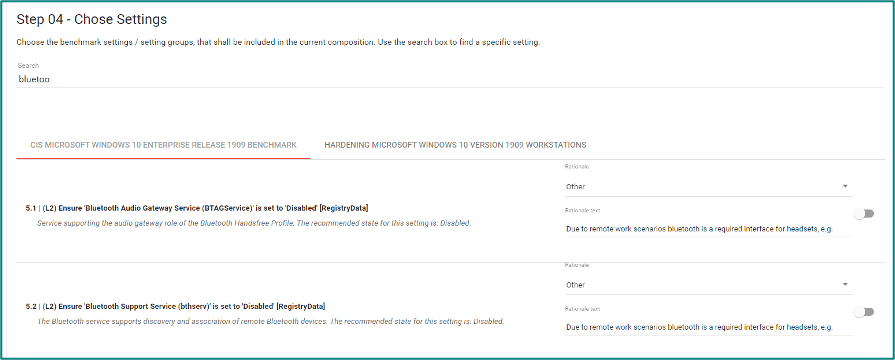
- However, before finalizing the hardening policy, an administrator may intentionally configure settings different from the default and document a reason for doing so.

- However, before finalizing the hardening policy, an administrator may intentionally configure settings different from the default and document a reason for doing so.
-
- Once the hardening baseline has been defined, the next step is to test the hardening set on a pilot server group. If no test environment is available, it is also possible to group individual systems into a test group and test the settings.
To do this, the affected systems must be added to the Enforce Inventory and the hardening assigned.
- Once the hardening baseline has been defined, the next step is to test the hardening set on a pilot server group. If no test environment is available, it is also possible to group individual systems into a test group and test the settings.
-
- If the test is completed successfully, the pilot group can either be extended or all affected systems can be supplied with the safety baseline. This means that the hardening is in operation and the next system group can be hardened.
- Run / Monitoring
- In service operations, compliance is monitored via various reports and dashboards. For example, if an administrator changes a setting on the target system without announcing this in the EA, the setting is automatically reset to the configured state and an alert is displayed in the dashboard.
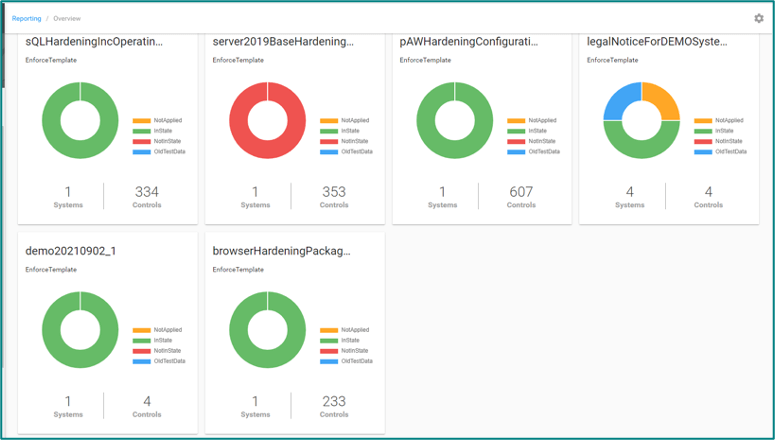
-
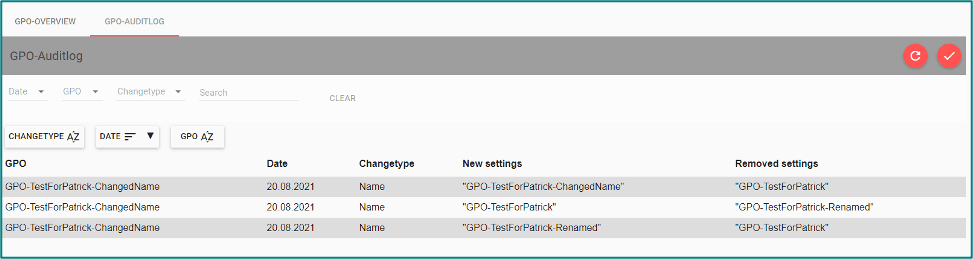
- It also often happens that settings are changed on GPOs that have an effect on the configured hardening set. This is also noticed and reported by EA. An administrator can then decide how to deal with the deviation.

- It also often happens that settings are changed on GPOs that have an effect on the configured hardening set. This is also noticed and reported by EA. An administrator can then decide how to deal with the deviation.
Summary and central safeguarding
At TEAL, we use the Enforce Suite approach, coupled with our services, to centralize the management of your IT systems’ hardening settings. Our goal is always to improve your infrastructure quickly, effectively and in a solution-oriented manner. Accidental changes to your system hardening settings are a thing of the past thanks to integrated self-monitoring.
You recognize some of these challenges and problems with yourself and would like to overcome the challenge of system hardening with the support of an experienced service provider? Our highly experienced IT consultants will be happy to advise you and give you initial recommendations on how to integrate the Enforce Suite in a preliminary discussion.
Optionally, our experts can provide services as part of managed services. The main aim here is to ensure that the Enforce Suite is operated properly.
Sieh dir diesen Beitrag auf Instagram an
Sieh dir diesen Beitrag auf Instagram an
LATEST POSTS
-
ESAE series part 1- Introduction
In the blog category "Secure Administration Environment" we want to share our experiences from customer projects around Microsoft's Enhanced Security Administration Environment ...
02 May, 2018 -
ESAE series part 2 – Customer situation and architecture
As announced in our introductory article on the ESAE series, we would like to elaborate on the client situation and the architecture of the solution in the second article....
03 May, 2018 -
ESAE series part 3 – Privileged access management & the shadow principal feature
As already announced in the last article (LINK) of the ESAE series, in this article we would like to give you a more in-depth description of the technical core ...
14 August, 2018