
17 May TEAL goes Service – we make security consulting concrete!
Managed services and intelligent products instead of pure consulting
Since our founding in 2017, a lot has happened at our company. Bit by bit, we have consolidated and expanded our expertise in the Microsoft ESAE
framework and the topic of “Securing Privilege Access”. At the beginning, we were still relying exclusively on the implementation of standard solutions from large manufacturers. However, it quickly became obvious to us that a standard solution quickly reaches its limits for our customers from the upper midmarket and the enterprise segment. This is partly because standard solutions can only meet the requirements of high-security environments to a limited extent, and partly because the solutions are usually too expensive for a dedicated small tier0 environment with < 50 servers.
Initially, we met the customers’ needs by implementing customized processes and partially automated workflows. Nevertheless, more and more the idea matured to support our customers with effective and highly efficient solutions.
We no longer want to pass on our accumulated experience and know-how in the area of Microsoft infrastructure and Active Directory security exclusively in a project implementation, but as a provider of special solutions we want to continuously increase the security in the customer environments.
For this reason, we are evolving from a pure consulting company to a provider of products and managed services and are growing beyond our previous consulting offering. In doing so, we want to keep adding new products and services to our existing portfolio in a meaningful way. Particularly important to us is the close partnership with other security specialists, with whom we offer and develop solutions together, in addition to our own complementary offerings and services.
We currently offer the following products and managed services:
Teal Security Assessment
With this assessment, we have developed a standardized procedure for analyzing your IT infrastructure. In three days, it will provide you with information on how attackers can gain access to your corporate network and how you can protect yourself against them. Always with the goal of mitigating the potential impact of an attack as much as possible.
We address the following topics:
-
- PREPARATION
In a workshop we explain how attackers behave, what the current threats are and how you can protect yourself.
- PREPARATION
-
- ANALYSIS
Next, we analyze your environment and document the current status.
- ANALYSIS
-
- PLANNING
Together, we define the appropriate countermeasures for your environment and create an implementation roadmap.
- PLANNING
-
- IMPLEMENTATIONWe firmly believe that only well-trained IT teams can effectively defend against cyber attacks. With the Security Assessment you lay the foundation to build up know-how and implement the first measures. We will gladly support you during the implementation or provide selective advice.

It has also proven successful to establish an iterative procedure in which measures are implemented, then the environment is analyzed again and new measures are derived. We are happy to support you here as well!
- Erhöhen Sie Ihre AD-Sicherheit mit unserem monatlichen TEAL Security Check.
- If you use Active Directory as the central identity management in your company, it has probably “grown historically” or has changed again and again due to acquisitions or sales. This is not surprising when you consider that Microsoft introduced Active Directory 20(!) years ago with Windows Server 2000. Therefore we recommend our customers to continuously check the security of the Active Directory and to implement improvements. The TEAL Security Check provides an overview of the current configuration, effectively detects errors contained therein and identifies important measures that improve the overall architecture. It also includes five important steps that should be performed on a monthly basis. Once the Security Check is established, it can be continuously expanded to include additional checks.
TEAL Audit Proof (TAP)
- With TAP, we simplify the entry into one of the most important topics for securing infrastructures – system hardening. As a founding member of the #NoCodeHardening initiative, we are driving the issue with our partners and want to educate about the topic and actively share our knowledge.
- But why is system hardening important? Not only since more and more cyber-attacks are published in the media and the costs of successful ransomware attacks are increasing, companies are dealing with the topic of system hardening. This involves the secure configuration of applications, clients, servers and cloud systems, which can be a complicated, complex and time-consuming process. Help in defining the correct settings is provided by numerous hardening standards, published by e.g. the German Federal Office for Information Security (BSI), the Center of Internet Security (CIS) or manufacturers such as Microsoft.
- With TAP, we have created the ability to create a compliance overview for individual systems. They can easily generate HTML reports and have a transparent overview of the compliance and non-compliance of explicit settings and configurations against industry standards and hardening guides. These reports can assist them in meeting compliance obligations or in compliance processes. Whereas these processes were previously time-consuming, they now determine this data automatically at the push of a button with our solution.
- You can use TAP free of charge and check your Windows 10, PAW, server or domain controller system against the industry standards we have compiled. Alternatively, we will be happy to support you and create a detailed evaluation and implementation recommendation that addresses your exact needs.
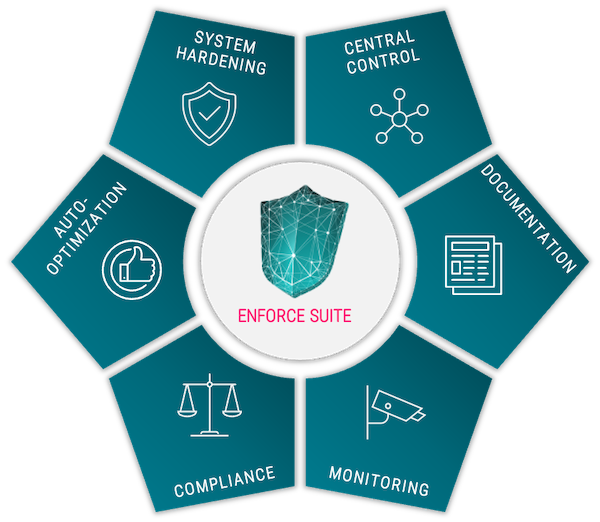
Enforce Suite
- Are you already familiar with the topic of system hardening and are faced with the challenge of defining a hardening standard and, above all, ensuring that ALL affected systems are and remain correctly configured?
Advantages & functions of the Enforce Suite::
-
- SYSTEM HARDENING
proven solution that hardens and securely configure your operating systems, browsers, office packages, among others, in accordance with established standards.
- SYSTEM HARDENING
-
- CENTRAL CONTROL
Enterprise-wide distribution of hardening and data protection settings.
- CENTRAL CONTROL
-
- DOCUMENTATION
Documentation and logs to meet mandatory proof requirements, e.g. under the DSGVO.
- DOCUMENTATION
-
- MONITORING
Depending on the expansion and usage, thousands of settings can be regularly checked and corrected.
- MONITORING
-
- COMPLIANCE
Demonstrable compliance with current laws and regulations based on industry-proven standards.
- COMPLIANCE
-
- AUTO-OPTIMIZATION
self-monitoring system where safety settings can be automatically set to the defined target state.
- AUTO-OPTIMIZATION
As mentioned above, we are continuously working on the expansion of our portfolio. Unfortunately, we can’t provide any details at this time, but we are proud and excited about this new partnership. We can tell you this much, EVERYONE who is involved in Active Directory security knows this company and their products. We are looking forward to the cooperation and the opportunity to offer the excellent solutions in Germany! 😊
You will learn more in summer at the latest…
With the highlighted offers we consolidate our consulting portfolio and bring the first own solutions to our customers. As always, our goal is to improve your infrastructure quickly, effectively and solution oriented.
We are on our way to make the transformation from a pure consulting service provider to a full managed service provider. At the same time, we do not forget where we come from, continue to grow organically and not at any price. As our customers, you will benefit from our many years of experience in the field of infrastructure security. In the future, you will be able to request products and managed services from us in addition to our traditional consulting services (SAE, SCI).
The foundation stone for the expansion of our portfolio has been laid. We are looking forward to publishing more information about the individual offerings piece by piece over the next few months. We are also curious to see how you will react to the current offers, as well as to the new ones.
Get in touch with us 🚀!
Sieh dir diesen Beitrag auf Instagram an
Sieh dir diesen Beitrag auf Instagram an
LATEST POSTS
-
(E) SAE DEEP DIVE SERIE Part 2 – Secured VMs in an ESAE environment with VMWare
In our January blog, we started an SAE deep dive series and explained how to use Hyper-V as a secure hypervisor in an (E)SAE scenario. Since by far not all our customers use Hyper-V, but many also use VMWare...
15 June, 2020 -
(E) SAE Deep Dive Series Part 1: Hyper-V Host Guardian Service (HGS) and Shielded VMs in an EASE Environment
After the success of the first ESAE series, we decided to launch a deep dive series in which we go into a little more detail on various measures....
16 January, 2020 -
(E) SAE DEEP DIVE SERIES Part 3 – Separate admin accounts
After Hyper-V HGS and VM protection with VMWare, now the third part of our (E) SAE Deep Dive Series follows. Maybe you follow us on LinkedIn, Xing, Facebook, Instagram or Twitter and ...
15 July, 2020





























