15 Nov The top 3 challenges of hardening with GPOs and how the Enforce Administrator solves them
After we dealt with the content challenges of system hardening last month, we want to deal with some technical and organizational topics this month.
This article can certainly be seen as an advertisement for the Enforce Administrator product, so let’s start by saying that we are convinced of the product, we are a partner company of the manufacturer FB Pro GmbH and we distribute the Enforce Administrator. We also offer the operation of the solution as part of a “managed service” for our customers.
Below we would like to describe the top 3 challenges when hardening with GPOs and show how the Enforce Administrator solves them. In addition, there are other topics that FB Pro highlights in this blog post, such as integration via Enforce Administrator REST API into various processes (e.g. server deployment, incident management). Also Microsoft has already written a few years ago an interesting comparison between GPOs and Powershell DSC, the technology on which the Enforce Administrator is built.
Challenges of hardening with GPOs
Rollback / testing is difficult
If you read last month’s blog article, you realize that you have a lot of testing to do before you can roll out final hardening across the enterprise.
Unfortunately, this turns out to be harder than it sounds. GPOs don’t provide a way to restore previous settings. Once the hardening settings are rolled out, the previous state is lost.
Usually, you then have to painstakingly dig through the Microsoft documentation to find out what the default setting is. This requires testing on a new system where you can be sure that Microsoft’s default state prevailed before. But let’s face it, hardening a new system in the default state is not a problem. Here everything still works after hardening. It only gets exciting when applications are installed that interact with the environment (cf. NTLM, SMB v1 etc. in the last blog article).
Such realistic tests can only be performed if you have a test environment that comes close to the state in production. Unfortunately, our experience shows that this is not the case for many companies.
If such a test environment is not available, sooner or later tests are performed on the live system. Then one can no longer be so sure that all 300+ settings of the baseline (e.g. CIS) have previously corresponded to the delivery state of Microsoft.
Enterprise-wide reporting is not possible
GPOs are unfortunately a fire-and-forget solution. Once configured, you have to rely on the GPO client to work correctly on all systems and set the settings as you specify. There is no central mechanism to verify that the settings on the systems actually match the desired configuration, let alone the ability to generate a corresponding report to present to an auditor, for example.
In our view, this will be an important issue for all companies that are ISO 27001 certified from 2023 onwards. As far as we know so far, the topic of system hardening including verification will become significantly more important in certification.
But even if you are not certified, it makes sense to ensure that the systems are configured as they should be.
Only (easily) usable for AD integrated systems
Group Policies are tightly integrated with Active Directory. The individual templates, as well as the policies, are stored on the domain controllers and retrieved there by the Group Policy Client, which is integrated into the operating system.
In principle, this is (was) a good thing. However, there are some scenarios where you don’t want to run Windows systems AD joined, e.g. in the DMZ. Recently, however, we have also encountered more and more customers who only join their end devices to Azure AD and manage them with Intune.
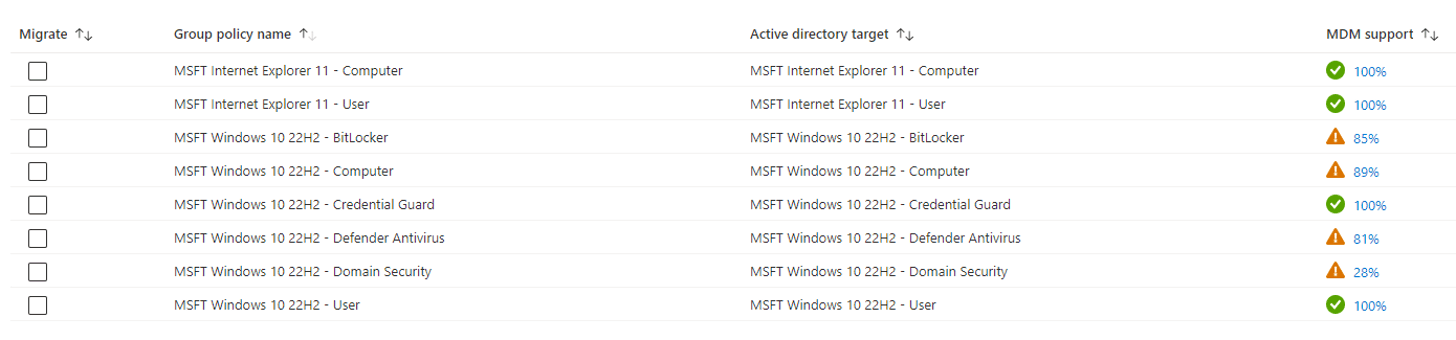
Now there are security baselines for Windows 10 and 11 for Intune as well, but there are SIGNIFICANTLY fewer settings than in the usual hardening standards. To verify this, we checked an endpoint hardened with Intune using our free Teal Audit Proof (TAP).
The result is sobering.
With the current security baseline from 22H2, there is quite a high percentage of settings that can also be set via Intune, apart from Domain Security.
However, the missing settings would first have to be painstakingly analyzed to find out whether they are relevant for the company.
Linux systems cannot be managed at all with GPOs; support for Linux clients has just been announced for Intune.
How does Enforce Administrator solve the challenges?
Rollback / Testing
The Enforce Administration has a very helpful backup / restore function. Each time a new configuration is rolled out, the current value of all settings that are changed are saved. These can be restored at any time.
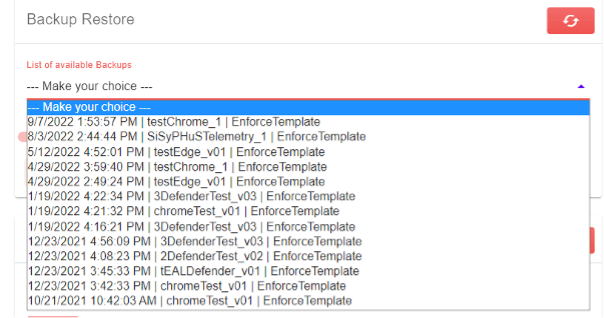
Even with this function, of course, a cleanly planned test procedure is necessary, but this functionality facilitates the work immensely.
Reporting
Reporting is divided into operational dashboards and configuration reports in Word format.
Operational dashboards
In the dashboard you can see (among other information) how many systems you have applied a configuration to and whether any deviating settings or out-of-date test data was detected on them. Sometimes it happens that a complete configuration cannot be applied. This is also shown:
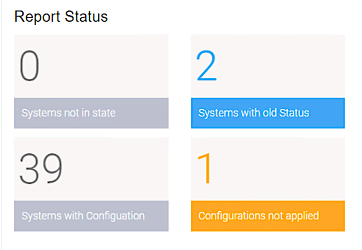
With the Overview Dashboard, you can tell at a glance whether the environment has a problem or not.
If something is not ok, you can get to the bottom of things in the detailed reporting dashboards.
In the Reporting Overview you can see the status of each hardening configuration:
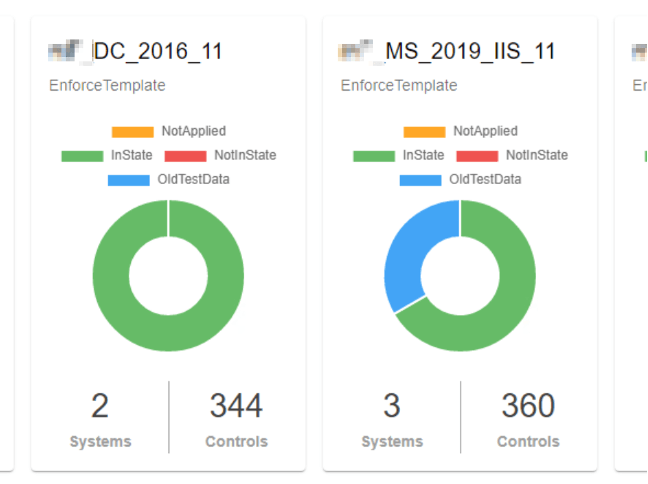
If you click into them, you can see which system has a problem:
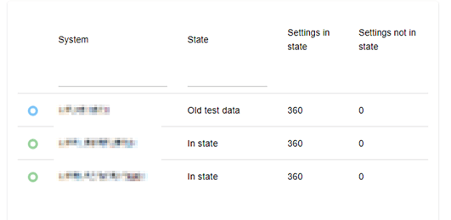
If you click on the system, you can see which settings are “In State” and “Not in State”:
With the dashboards, you can find out which setting is making a problem with just a few clicks.
The dashboards are helpful for operations, an auditor would want to have this information in a document and not look it up in the live system. For this scenario, Enforce Administrator provides two report types.
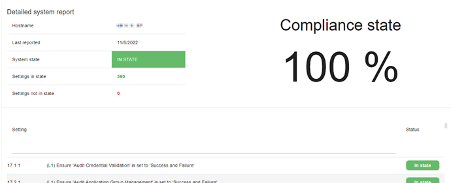
The system report shows what configuration(s) are applied to the system and the status of the settings:

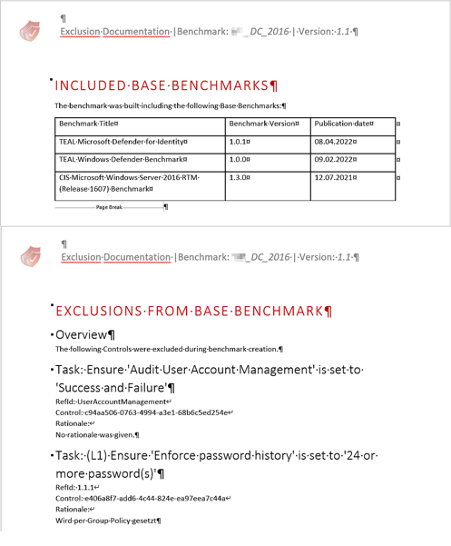
Beyond that, however, an auditor still wants to know what deviation the configured hardening has to the benchmarks of the various manufacturers and why. The Exclusion Report answers this question:
Non-AD systems
The Enforce Administrator also works completely without a domain. Only two ports in the firewall are required for communication (WinRM and NuGet). Authentication is then done with local accounts:
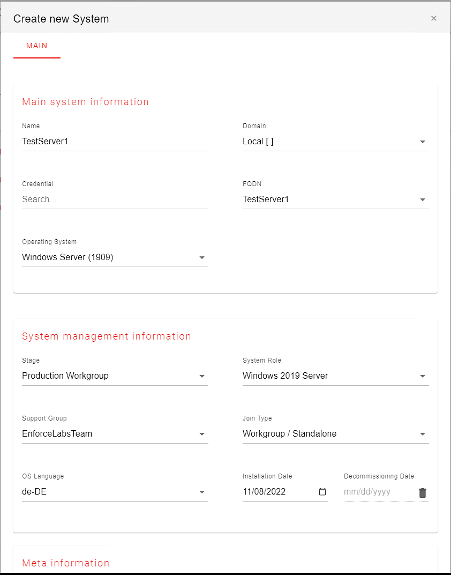
In addition to domain and workgroup, the AzureAD, Intune and Hybrid Azure AD scenarios are also possible:
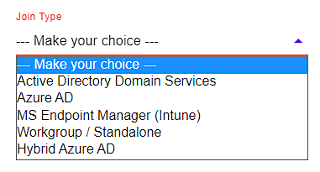
However, all of them (still) require that the systems have a network connection with name resolution to the Enforce Administrator server.
The management within the Enforce Administrator is completely the same apart from the authentication configuration.
Besides all the Windows scenarios, hardening of Linux systems is also on the FB Pro roadmap. This is possible because the Enforce Administrator is based on PowerShell DSC and PowerShell (Core) is also available on many Linux distributions.
Conclusion
The hardening tool solves some essential problems of GPOs and is therefore a great help in the toolbox of every IT department. Hardening systems becomes much easier with the Enforce Administrator. However, good planning and structured implementation are still necessary (especially in the enterprise environment). We would be happy to help you with this or with the operation of the hardening solution.
Sieh dir diesen Beitrag auf Instagram an
Sieh dir diesen Beitrag auf Instagram an
LATEST POSTS
-
Behind the scenes of our security assessment
Today we want to take a look behind the scenes of our security assessment, but what is it anyway? In a nutshell, we enable you to make informed decisions and base your next steps on a solid, risk-aware foundation....
15 April, 2024 -
Pwned by the Mail Carrier
How MS Exchange on-premises compromises Active Directory and what organizations can do to prevent that. SpecterOps recommends their customers establish a security boundary around their most critical assets (i.e., Tier Zero) of Active Directory (AD). ...
04 April, 2024 -
secIT 2024: Focus on system hardening
Together with one of our partners FB Pro, we will be at stand 58 in the Eilenriedehalle in the Hannover Congress Centrum. Our focus will be on a central topic that is of crucial importance in the cyber security world: system hardening...
15 February, 2024