
12 Nov Troubleshooting Bitlocker on Server 2019 Core
Update: 08.01.2020
Today we received a short update from Microsoft including an easier workaround. The problem as such is unfortunately not yet solved.
The easy workaround is as follows:
Bitlocker can be enabled, without uninstalling the Feature on Demand Packages if you configure the following Group Policy as shown in the screenshot:
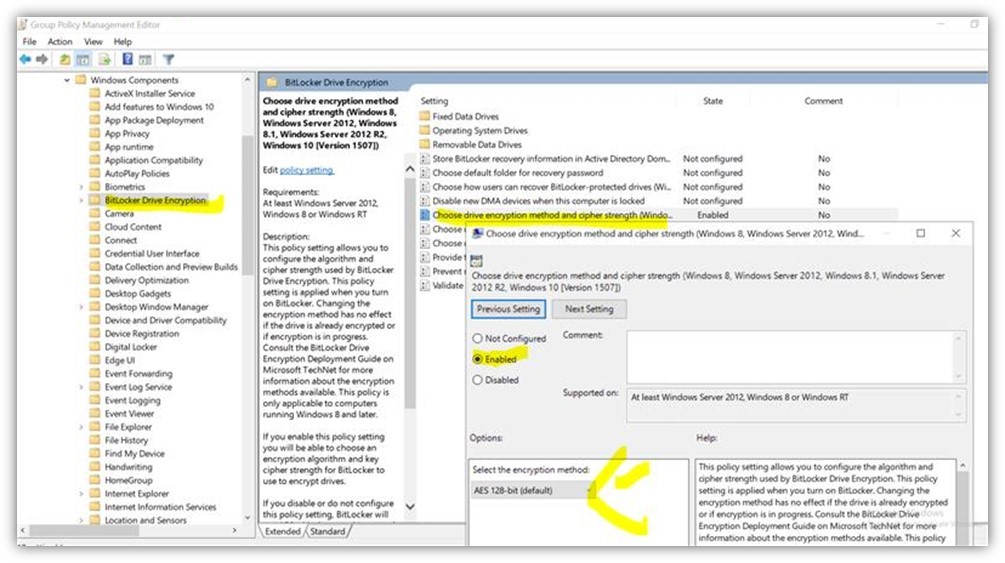
Microsoft explained that with the policy configured the path to the executed code changes and as a result the error does not occur. It doesn’t matter with encryption algorithm is used.
Original article from 12.11.2019
In one of our SAE projects we have once again discovered an interesting problem. This time it is about a bug in the interaction of Windows Server 2019 CORE, Bitlocker and the App Compatibility Feature from Microsoft.
Problem
In our SAE architecture, we use Server 2019 Core Edition. To still open some graphical consoles, we use the Server Core App Compatibility Feature on Demand. This makes it possible to use tools like the MMC console, the Eventviewer, PowerShell ISE and some more on a CORE system.
Furthermore we want to encrypt our drives with Bitlocker. Usually a simple operation. However, when using the PowerShell command, we got the following error message:
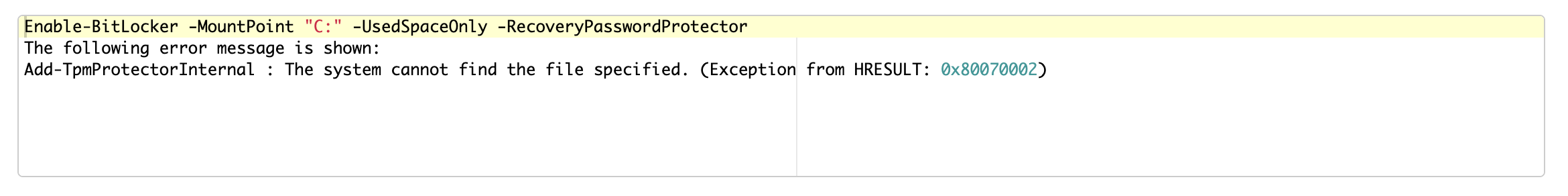
After a reboot we received the following error message:

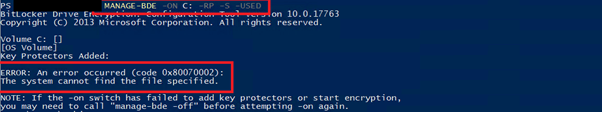
Also with the command “manage-bde -on C: -RP -S -USED” we had no success:
Solution
A final solution is not yet available. The bug has been escalated to the Microsoft Engineering Team. Microsoft is currently working on a solution and will probably release an update.
In order to move on in our project, we have developed the following workaround:
1. uninstalling the App Compatibility feature:
Remove-WindowsCapability -online -Name ServerCore.AppCompatibility~~~~0.0.1.0
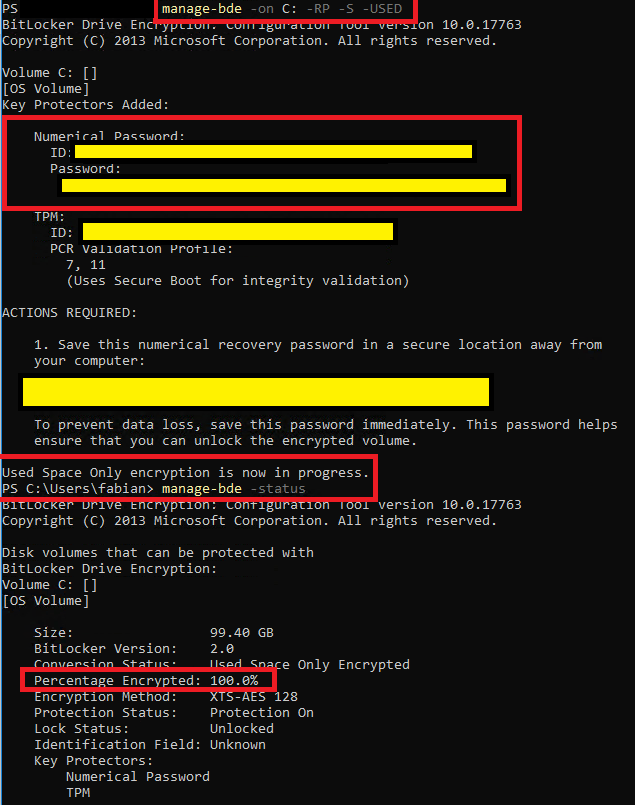
2. bitlocker encryption of all drives. Here is an example screenshot of the system partition:
3. reinstalling the App Compatibility feature:
Add-WindowsCapability -online -Name ServerCore.AppCompatibility~~~~0.0.1.0
Sounds like a very simple workaround at first. But since we invested a lot of effort (TPM reset, repair installation etc.) to identify the bug, we want to inform you about this workaround.
Source: freepik.com
LATEST POSTS
-
(E) SAE DEEP DIVE SERIE Part 2 – Secured VMs in an ESAE environment with VMWare
In our January blog, we started an SAE deep dive series and explained how to use Hyper-V as a secure hypervisor in an (E)SAE scenario. Since by far not all our customers use Hyper-V, but many also use VMWare...
15 June, 2020 -
(E) SAE Deep Dive Series Part 1: Hyper-V Host Guardian Service (HGS) and Shielded VMs in an EASE Environment
After the success of the first ESAE series, we decided to launch a deep dive series in which we go into a little more detail on various measures....
16 January, 2020 -
(E) SAE DEEP DIVE SERIES Part 3 – Separate admin accounts
After Hyper-V HGS and VM protection with VMWare, now the third part of our (E) SAE Deep Dive Series follows. Maybe you follow us on LinkedIn, Xing, Facebook, Instagram or Twitter and ...
15 July, 2020




























