
15 Sep Secure your Azure and On-Prem environments!
 In March of this year, we announced our partnership with Specterops, and since then at the latest, the topic of Attack Path Management (APM) and BloodHound Enterprise has been very much with us. We have already launched some joint activities, such as our webinar, or a joint blog article. Our T-shirt campaign, with which we wanted to make a small contribution to the management of the Ukraine crisis, was also a great event that we look back on with pleasure.
In March of this year, we announced our partnership with Specterops, and since then at the latest, the topic of Attack Path Management (APM) and BloodHound Enterprise has been very much with us. We have already launched some joint activities, such as our webinar, or a joint blog article. Our T-shirt campaign, with which we wanted to make a small contribution to the management of the Ukraine crisis, was also a great event that we look back on with pleasure.
In addition to the planned actions, we also regularly work together on customer inquiries, demos or troubleshooting around BloodHound Enterprise.
In this blog article we would like to talk about how easy it is to try BloodHound Enterprise and get convinced of its numerous benefits. We’ll explain the requirements for a free trial and how you can get the most out of it.
What is BloodHound Enterprise?
BloodHound Enterprise is a tool that identifies attack paths and provides assistance in resolving them. Attack paths are nothing new ❯ identity-based attack paths have long been common knowledge and are analyzed in depth by both attackers and defenders. You can see an example of an attack path here:
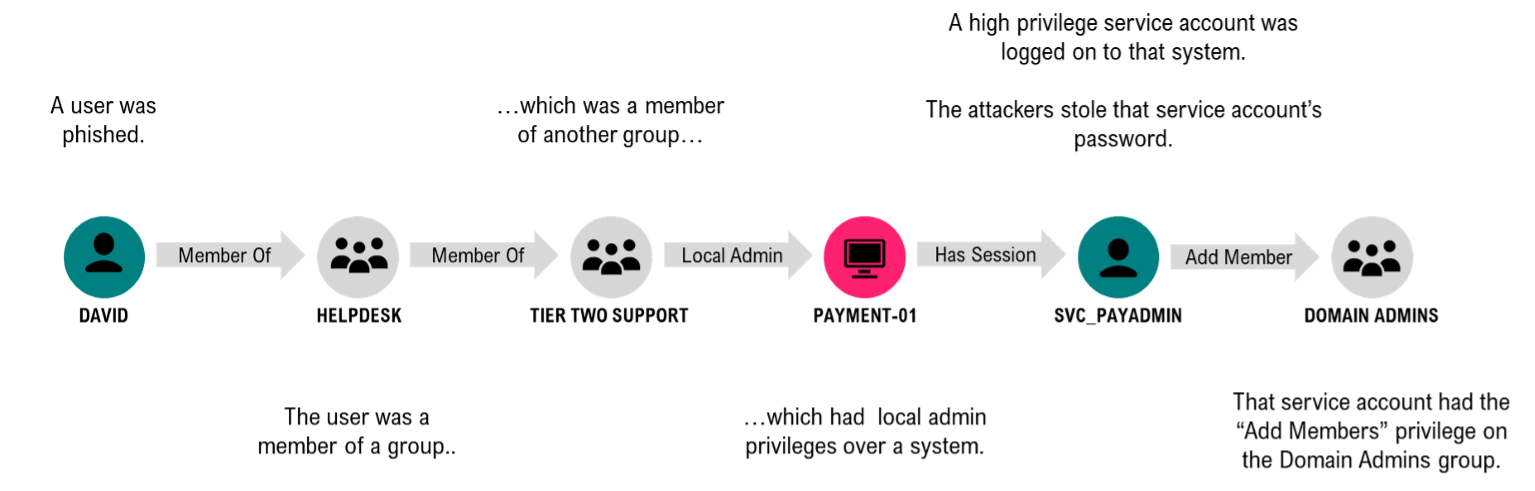
BloodHound Enterprise is an “Attack Path Management” tool whose methodology enables organizations to understand attack path risks, empirically quantify their impact, and eliminate them. The primary goal of APM is to directly resolve attack paths, as they are a huge problem in the Microsoft Active Directory and Azure Active Directory world. These services are the most lucrative for attackers because control of an enterprise is enabled by the controllers of these systems.
How does BloodHound Enterprise work?
BloodHound Enterprise is a cloud solution that automatically analyzes and prioritizes existing data in an environment and identifies possible solutions.
Attack paths can thus be reported and remediated quickly and in near real-time.
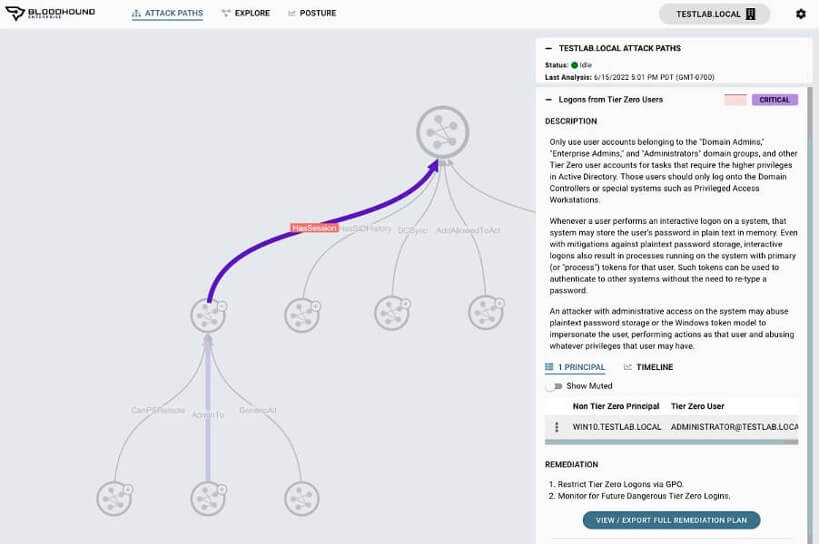
In order for the data to be analyzed, the environment must be connected to the BloodHound Enterprise Tenant. It is possible to connect multiple Active Directory or Azure Cloud environments. Let’s first look at how one would connect an on-prem AD structure.
ON-PREM connection

Those who have studied the open source variant of Bloodhound in depth will already be familiar with the SharpHound Data Collector. Bloodhound Enterprise collects the data with the help of the SharpHound Enterprise Service. One or more collectors can be installed on different Windows machines. These connectors then establish an outbound connection via port 443 to the BloodHound Enterprise tenant. The connection is appropriately secured via TLS1.2.
To read out the environment data, a distinction must be made between two data types. On the one hand there is so-called “AD Structure” data and on the other hand “Privileged” data.
AD structure data
This data contains all AD objects that are located in the Active Directory database. E.g. users, groups or computer accounts, but also OU or GPO objects. To be able to collect this data, the SharpHound service must be able to talk to any domain controller via port 389. The data itself is by default available for reading to any authenticated user. It is therefore sufficient to grant the service account “normal” domain user permissions for this.
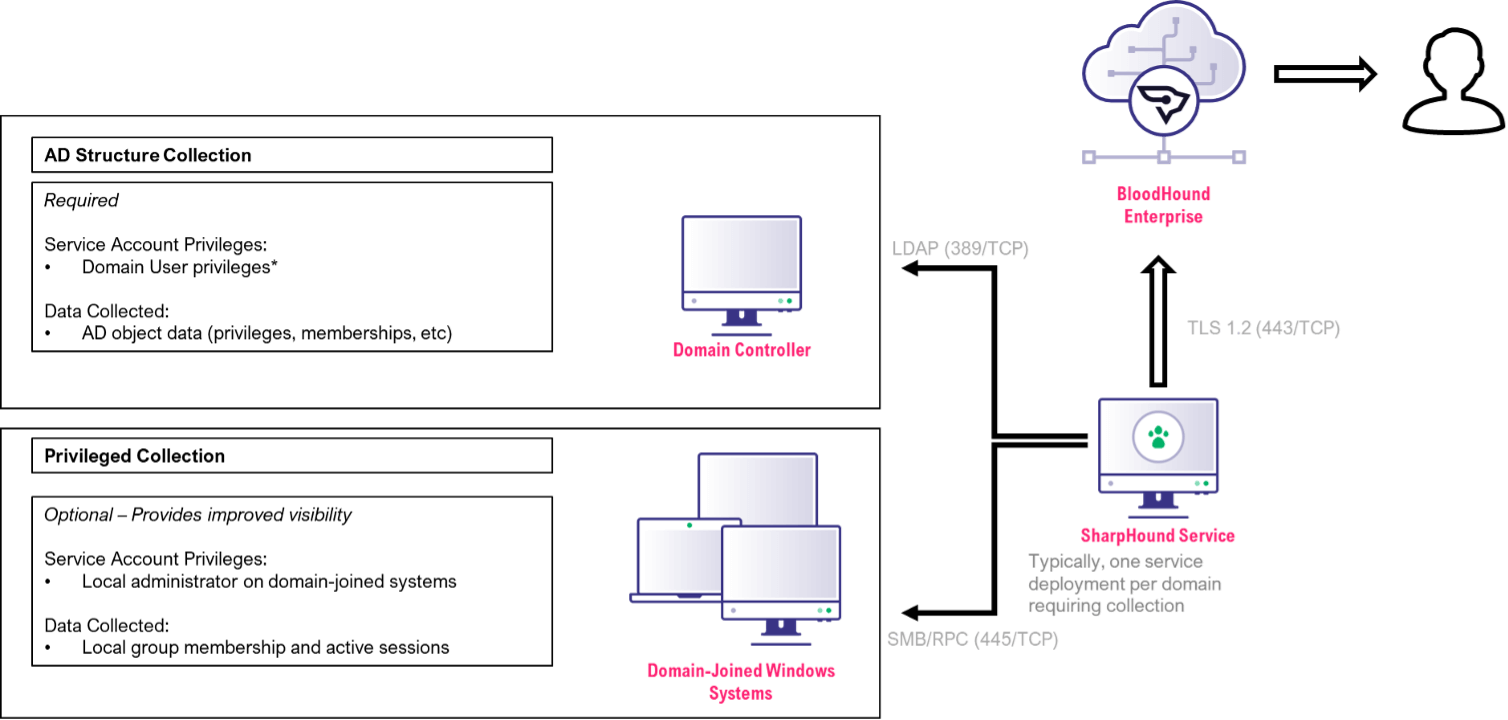
Privileged Data
 The situation is somewhat different with the so-called Privileged Collection, where both the local group memberships and the active logon connections are to be read out from each domain member, i.e. servers, clients, tablets, etc. The Privileged Collection is also used to analyze the active connections. Especially the active connections are very important for the attack path analysis. If, for example, a highly privileged account is logged on to a “normal” end user system, this often results in completely new attack paths that would not have been possible without this incorrect logon.
The situation is somewhat different with the so-called Privileged Collection, where both the local group memberships and the active logon connections are to be read out from each domain member, i.e. servers, clients, tablets, etc. The Privileged Collection is also used to analyze the active connections. Especially the active connections are very important for the attack path analysis. If, for example, a highly privileged account is logged on to a “normal” end user system, this often results in completely new attack paths that would not have been possible without this incorrect logon.

Depending on the Windows version, local administrator rights are required for these queries. Systems < Windows 10 build 1809 still give this information to any authenticated user.
It is a bit tricky to give a single user local admin permissions on all server and client systems. Therefore, we recommend the following solution option for productive use.
A dedicated SharpHound agent is installed for each tiering stage. For each stage a separate user is configured, who has local admin rights on the respective systems. This ensures that, for example, Tier0 systems are scanned by a Tier0 user and Tier1 systems are scanned by a Tier1 user. This approach greatly reduces the importance of SharpHound service accounts and provides the ability to process relevant data in a tiering-compliant manner.
To connect the local agent to the BloodHound Enterprise Tenant, an agent must be created in the tenant and a unique key must be stored in the local client. In addition, it is specified which data is to be collected and how often.
AZURE connection
The connection to an Azure environment, is handled by the AzureHound service. The AzureHound Enterprise service collects data about the Azure environment and uploads it to the BloodHound Enterprise instance for processing and analysis.
AzureHound Enterprise is typically deployed on a single Windows system per Azure tenant and can run on the same system as the SharpHound Enterprise service.
Network connections via port 443 to the BloodHound and Azure tenant are required for operation. Again, traffic is protected using TLS.
Within Azure, read permissions to the Azure AD Tenant, Azure Subscription and Directory ReadAll permissions in Microsoft Graph are required.
The installation itself consists of the following elements:
-
- Creating an AzureHound enterprise app in the Azure tenant.
- Assigning permissions within Azure
- As well as installing the AzureHound agent on a local Windows machine
Now that we have clarity on the technical requirements, how does a BloodHound Enterprise Trial actually work?
Trial procedure
Running a trial gives you the opportunity to become familiar with the product while our team of experts helps you set it up and answer any questions that arise.
At the end of the day, no demo, presentation, or white paper is going to be able to explain a product like simply deploying it in your environment. Whether we do the trial in a test environment, or the production environment, is up to you. From our point of view, however, it is recommended to perform the analysis in the productive environment. APM is about identifying and eliminating real threats. In test environments, there is usually much less “legacy” and historically grown configurations. Any finding that is fixed in production can ideally stop an attacker.
The trial is conducted over a 14-day period and includes the following phases:
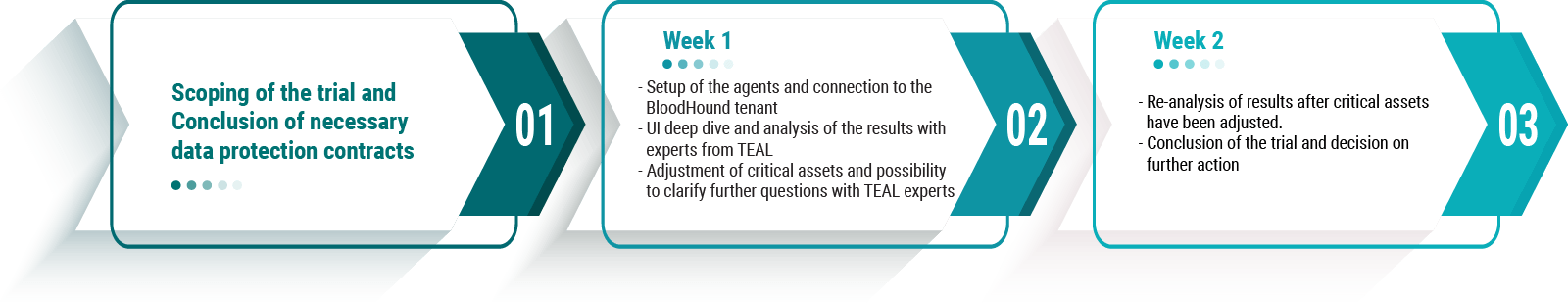
The first step is to determine which environments are to be analyzed in the trial. In addition, we conclude appropriate data protection agreements with SpecterOps and you, which regulate the handling of your data. Subsequently, we jointly determine the start for the trial and create the tenant in the background.
After that, the first week of the trial will start, where we will guide you to deploy the agents and connect them to the tenant. In the run-up to our next appointment, we analyze the attack paths we found. In the appointment itself, we will present the entire UI of BloodHound Enterprise and give an assessment of the results. In the same session we will also give you your own user accounts, so that you can work with the results yourself afterwards.
In a second appointment in the first week we will meet again and answer any questions that may have arisen. In addition, we will configure further critical assets together in order to obtain as complete an overview as possible.
The second trial week, begins with the third of a total of four meetings. In this meeting, we will check which attack paths have been added since the critical assets were changed and will again be available to answer your questions.
In the last meeting at the end of week two, we recap the trial and decide together on the next steps. Ideally, the tenant will just keep running and the productive phase of BloodHound Enterprise can begin.
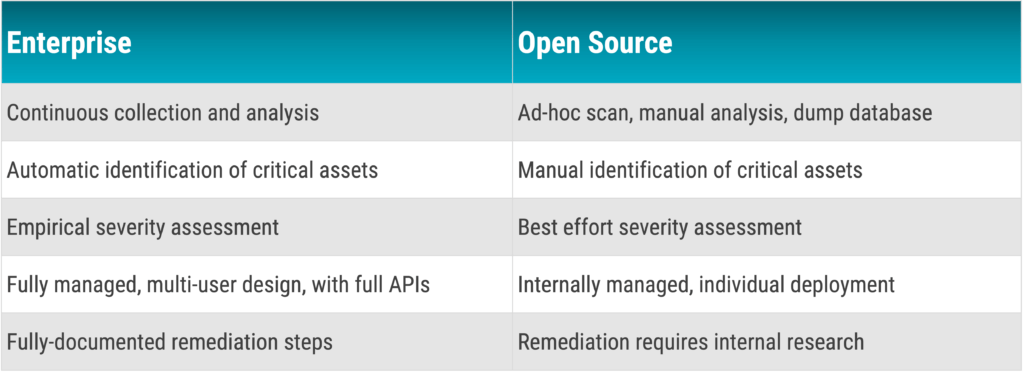
Why Enterprise and not open source version?
In our opinion, BloodHound Enterprise has some advantages over the open source variant. In principle, it also offers the possibility to analyze an AD environment, but it is much more time-consuming to come to the right conclusions. In summary, we see the following advantages of the Enterprise variant:
How do I start a trial?
If you are interested in learning more about BloodHound Enterprise, or if you want to start a trial right away, feel free to contact us. We are always available via the contact form or by phone.
Of course you can also call us at any time
spontaneously call us or send us an email.
TEAL Technology Consulting GmbH
Breite Str. 22
40213 Düsseldorf
E-Mail: info@teal-consulting.de
Phone: +49 (0)211 936 75 225

Of course you can also call us at any time spontaneously call us or send us an email.
TEAL Technology Consulting GmbH
Breite Str. 22
40213 Düsseldorf
E-Mail: info@teal-consulting.de
Phone: +49 (0)211 936 75 225
AUS UNSEREN SOCIAL MEDIA KANÄLEN
Sieh dir diesen Beitrag auf Instagram an
Sieh dir diesen Beitrag auf Instagram an
LATEST POSTS
-
Behind the scenes of our security assessment
Today we want to take a look behind the scenes of our security assessment, but what is it anyway? In a nutshell, we enable you to make informed decisions and base your next steps on a solid, risk-aware foundation....
15 April, 2024 -
Pwned by the Mail Carrier
How MS Exchange on-premises compromises Active Directory and what organizations can do to prevent that. SpecterOps recommends their customers establish a security boundary around their most critical assets (i.e., Tier Zero) of Active Directory (AD). ...
04 April, 2024 -
secIT 2024: Focus on system hardening
Together with one of our partners FB Pro, we will be at stand 58 in the Eilenriedehalle in the Hannover Congress Centrum. Our focus will be on a central topic that is of crucial importance in the cyber security world: system hardening...
15 February, 2024




























